 |
Tech Tip - Understanding How Traffic Prioritization Uses IP Port Ranges |
 |
Tech Tip - Understanding How Traffic Prioritization Uses IP Port Ranges |
DynamicAccess software supports the emerging 802.1p/Q standard to provide Traffic Prioritization over Ethernet networks. The 802.1p standard allows up to eight levels of priority to be defined according to business needs. This is accomplished by looking in the packet at the specific IP port number of the application to be prioritized and applying the proper classification tag.
IP port numbers are used to set up sessions at the transport (TCP/UDP) level. In addition to knowing the IP address of the remote system, an application also needs to know how to address the specific program with which it wishes to communicate. The application reaches the other program by specifying a service port, which is a 16-bit number that uniquely identifies an application running on the system. The port numbers are divided into three ranges: the Well-Known ports, the Registered ports, and the Dynamic and/or Private ports. The ranges are:
The Well-Known ports numbers are assigned by the Internet Assigned Numbers Authority (IANA). On most systems these ports can only be used by system (or root) processes or by programs executed by privileged users. The Registered Ports are also listed by the IANA. On most systems, the registered ports can be used by ordinary user processes or programs executed by ordinary users. Because of their nature, Dynamic or Private ports are not listed under the IANA.
DynamicAccess software Traffic Prioritization provides MIS managers with a built-in list of common, commercial applications with IP port numbers. This list is found in the DynamicAccess Control Panel utility. However, not all software vendors have registered their applications with the IANA, so there might be applications not listed in the DynamicAccess software Control Panel utility. In other cases, applications use a dynamic port number that is defined when the application is installed in the network. Such applications include, for example: Remedy Action Request System, Medicode PowerTrak, PeopleSoft HMRS and Financials, Scopus SupportTEAM, MedicaLogic LinkLogic, Clarify ClearQuality and ClearSupport, SAP/R3 and BEW, 3M LifeTime Data Repository, and BEA Tuxedo. Some of these applications rely on the IP port number used by the database application they use, such as Oracle SQL*Net or Sybase SQLServer.
Regardless, DynamicAccess software allows customers to add new applications. To add their applications, network managers need to know the IP port number of the application to be added. If the number is not known, in some cases it can be found at:
ftp://ftp.isi.edu/in-notes/iana/assignments/port-numbers%7E
http://www.cernet.com.br/Livingston/Filtros/reg_wkpn.txt
http://www.con.wesleyan.edu/~triemer/network/docservs.html
http://www.chebucto.ns.ca/~rakerman/port-table.html
If an application is not listed, the application's vendor may know the application's port range. However, this may not be the easiest way to find out that information. As a last resort, you can use a protocol analyzer to find out the port number that applications use in your specific environments.
A variety of software-based protocol analyzers can be used if you do not have one already. Some of these analyzers can be found at:
ftp://ftp.simtel.net/pub/simtelnet/msdos/lan/ethld200.zip (from http://www.sni.be/as-ref/)
The network administrator needs to look at the TCP/UDP level for the IP port number that is included in the TCP/UDP header:
Local Network |
IP Header | UDP
or TCP |
Application
|
Local
Network |
| UDP Datagram or TCP Segment | ||||
| IP Datagram | ||||
Local Network Frame |
||||
The previous diagram shows the three different levels of addressing schema used between end systems in network communication. At the Ethernet level, the MAC address identifies physical devices, and the MAC address is physically configured on the network interface card or device port. The next level, IP, uses IP addresses to identify the network and hosts that the process is running on. The UDP/TCP address identifies the user process or application based on the UPD/TCP port numbers. As shown in the next diagram, these port numbers occupy the first 32 bits of the UDP or TCP header, 16 bits (0 to 15) for the Source Port and 16 bits (15-31) for the Destination Port.
1 - 15 Source Port |
16
- 31 Destination Port |
32 - 47 bits Length Checksum UDP Data |
UDP (User Datagram Protocol) Header |
||
1 - 15 Source Port |
16
- 31 Destination Port |
32 - 63 bits Sequence Number Acknowledgement Number Data |
TCP (Transmission Control Protocol) Header |
||
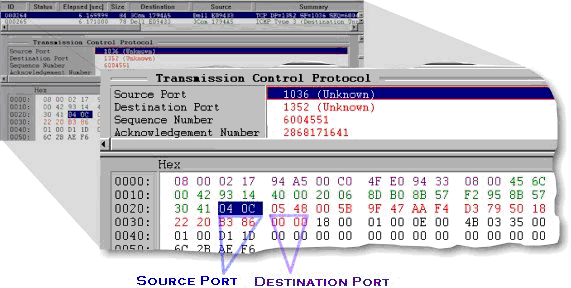
Converting the hexadecimal value of the UDP/TCP port number to a decimal number provides the value that has to be entered into the DynamicAccess software Control Panel utility to add a new application.
Copyright ©1998, 3Com Corporation.
Unless otherwise indicated, 3Com registered trademarks are registered in the United States
and may or may not be registered in other countries. 3Com, DynamicAccess,
EtherDisk, EtherLink, LinkBuilder, OnCore, SmartAgent, and SuperStack are registered
trademarks of 3Com Corporation. CoreBuilder and PACE are trademarks of 3Com Corporation.